 BreachBeagle
BreachBeagle
A free tool monitoring access to infrastructure configuration
Don’t miss unauthorised access to your IT premises. Hide fake database credentials that spot hackers’ attention. Get notification whenever someone tries to use them.
FAQ
How does it work?
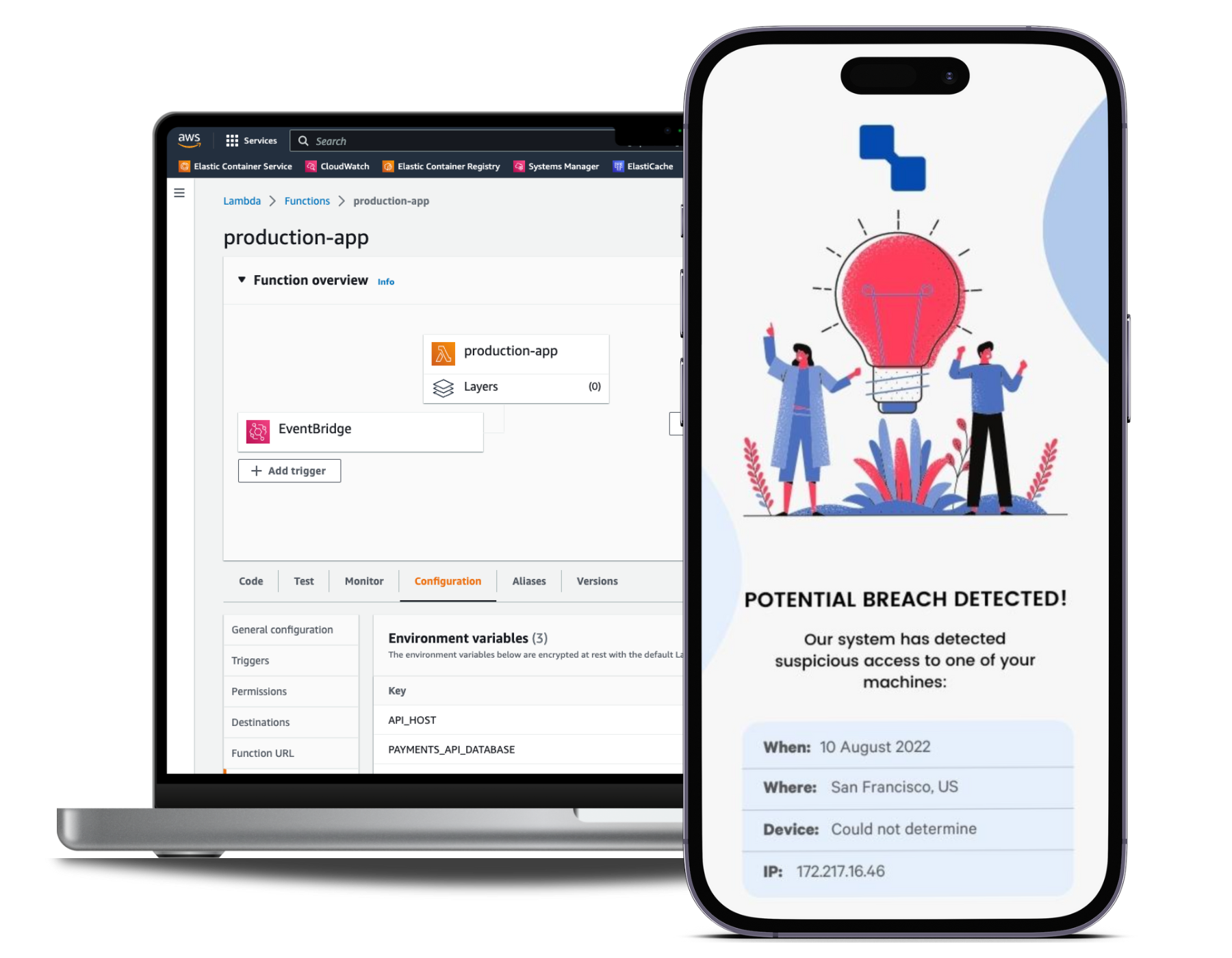
BreachBeagle generates fake database credentials that attract hacker's attention. Once the attacker tries to access our honeypot, we notify you about potential breach in you system.
How do I install it?
BreachBeagle installation is dead simple. All you have to do is add our fake postgres configuration to your config file, such as AWS Lambda Secrets, .ENV file, etc.
Is it secure?
Our service cannot read your Cloud configuration or access your IT premises. It can only passively listen to incoming traffic and terminate all connection attempts. If you wish to self-host solution for greater control, reach out to us!
What is a lateral movement?
Lateral movement is a technique used by cyberattackers who, after gaining initial access, search for sensitive data and other high-value assets, often with a support of automated scanners.